Introduction:
In the landscape of cloud services, Azure Application Gateway has consistently piqued my interest. This blog is a testament to my admiration for this service, which, in my experience, surpasses the traditional role of a load balancer. Its capabilities are often comparable to those of an F5 Advanced Web Application Firewall (WAF), which is saying a lot given the benchmark that F5 sets in the industry.
The Strengths of F5 Advanced WAF:
To set the stage, it’s worth noting the strengths of F5 Advanced WAF. Known for its solid security measures against web-based attacks and vulnerabilities, it also excels in load balancing and performance optimization. Its ability to be customized for specific security needs and its comprehensive reporting for compliance make it a strong contender in the web security domain.
Azure Application Gateway: A Step Beyond
Where Azure Application Gateway shines, however, is in its multifunctionality. Not just a mere traffic manager, it integrates the roles of a Web Application Firewall and a load balancer, ensuring top-notch security along with efficient application performance. Features like autoscaling, zone redundancy, and SSL offloading highlight its advanced capabilities. Moreover, the ease of integration with other Azure services simplifies management and deployment, making it a robust and versatile tool in any cloud infrastructure.
A Personal Testament:
In a recent project, the Azure Application Gateway stood as the linchpin. It served as the solitary entry point to a virtual network, safeguarding it from the vulnerabilities of the public internet. This configuration allowed for the adoption of a new IP address scheme, remarkably, without the need for a NAT gateway. It was a move that fortified the network’s security and enhanced its overall efficiency and scalability.
Let’s dive into some of its standout capabilities:
1. Autoscaling:
- What It Is: Autoscaling in Azure Application Gateway is a feature that automatically adjusts the gateway’s performance capacity based on current traffic loads.
- How It Works: This dynamic scaling ensures that the gateway can handle sudden spikes in traffic without any manual intervention. It scales out (adds more instances) during traffic surges and scales in (removes instances) when the demand decreases.
- Benefits: The primary advantage of autoscaling is its cost-effectiveness and efficiency. Users pay only for the resources they use, and the seamless scaling helps maintain consistent performance and availability of applications, even under varying load conditions.
2. Zone Redundancy:
- What It Is: Zone redundancy is a feature that enables the Application Gateway to be highly available across multiple Availability Zones in the same region.
- How It Works: By distributing the gateway instances across different zones, Azure ensures that even if one zone experiences an outage, the gateway continues to function using the instances in the other zones. This setup adds an extra layer of failover capability.
- Benefits: The primary benefit is enhanced resilience and availability. With zone redundancy, businesses can be assured of continuous operation and minimal downtime, which is crucial for critical applications and services.
3. SSL Offloading:
- What It Is: SSL offloading refers to the process of terminating SSL connections at the Application Gateway level instead of the web server.
- How It Works: In this process, SSL encrypted traffic is decrypted at the gateway and sent as plain traffic to the web servers. This offloading reduces the CPU load on the servers because they no longer have to encrypt and decrypt traffic.
- Benefits: The key benefit here is improved server performance and efficiency. By offloading SSL processing to the gateway, web servers can dedicate more resources to delivering content, leading to faster response times and an overall better user experience.
Leveraging Azure Application Gateway and Azure Front Door for Advanced Network Management:
In a significant development, Microsoft Azure has enhanced the capabilities of its Application Gateway through the introduction of an ‘enhanced network feature’. This feature ushers in a private variant mode, eliminating the need for a public IP address and bolstering security for internal network services. This advancement is particularly beneficial for organizations looking to differentiate between internal and external traffic, allowing for distinct and secure handling through tailored rulesets.
With the enhanced network feature, the Application Gateway steps into a fully private role, adept at guarding internal services against both egress and ingress traffic. This is a crucial development for internal network security, providing a more controlled and secure environment.
Integrating Azure Front Door into this setup extends these capabilities. Azure Front Door can be seamlessly blended with one or several private Application Gateways, enabling global distribution of services while maintaining localized control. This combination facilitates not just extended reach but also ensures that each zone is securely managed with its dedicated IP plan.
Consider a typical setup where internal backend services are placed behind the Application Gateway, which functions as a load balancer within its own dedicated zone. This zone is configured with a specific WAF ruleset tailored for internal traffic management, ensuring that internal communication is secure and efficient.
For external traffic, the integration of Azure Front Door introduces an additional layer of security. A different set of WAF rules in prevention mode is employed to manage external requests. This setup is designed to block unwanted requests and can leverage features like geo-matching to restrict access from specific regions around the world.
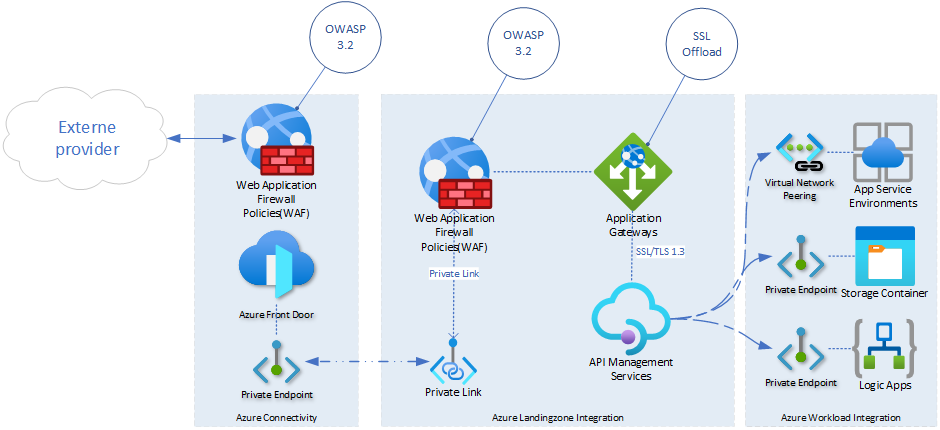
The dual-layer approach to security becomes evident here. While internal traffic from the data center, through VPN and ExpressRoute, is handled with a more ‘trusted’ ruleset, external traffic is subjected to more stringent security protocols. This method ensures that while internal services can be accessed securely and directly, external access is tightly controlled and monitored for any potential threats.
By combining Azure Application Gateway with Azure Front Door, organizations can create a robust, secure, and efficient network architecture. This architecture not only caters to both internal and external web traffic needs, but does so with a level of precision and reliability that is essential in today’s digital landscape.
A Critical Security Update:
In the continuous improvement, Azure has recently deployed an update to security against the CVE-2023-50164 vulnerability. This step involves a new managed rule in the Azure regional WAF.
The update, available in the Default Ruleset (DRS) version 2.1 and Core Ruleset (CRS) versions 3.2 and 3.1, is pivotal for customers who might be susceptible to this exploit. Azure advises changing the action of this rule from log to block to ensure enhanced protection. However, it’s important to note that the anomaly score action is not supported for this rule and that it is only applicable to WAFv2. Those using older versions will need to upgrade to leverage the block mode effectively.
This update is a crucial reminder of the evolving nature of web security and Azure’s diligent efforts to stay ahead of potential threats.
Conclusion:
The Azure Application Gateway is more than a load balancer; it’s a testament to the sophistication and adaptability of Azure’s cloud offerings. With each update and feature enhancement, it cements its role as a comprehensive solution for modern web applications, balancing impeccable performance with unwavering security.
