Introduction
In the era of digital transformation, organizations are incessantly exploring avenues to foster collaboration and enhance productivity. Azure Active Directory (AD) B2B collaboration emerges as a pivotal solution, enabling secure access and sharing of resources across organizational boundaries. This blog post aims to explore the intricacies of Azure AD B2B, its multifaceted benefits, potential downsides, and a simplified guide to getting started.
Section 1: Why Azure AD B2B?
Subsection 1.1: Bridging Organizations
Azure AD B2B is not merely a feature; it’s a bridge that connects disparate organizational islands, facilitating secure and seamless access to resources. External users can access an organization’s data, applications, and workflows without being a part of its domain, ensuring that collaborations are not hindered by technological barriers.
Subsection 1.2: Enhancing Collaboration
The essence of Azure AD B2B lies in its ability to foster collaboration by securely sharing applications and services with guest users. A notable example can be drawn from the Ministry of Justice and Security, which leveraged Azure AD B2B to grant external partners secure access to its internal project management tools, thereby streamlining project collaborations and ensuring timely deliveries.
Section 2: The Multifaceted Benefits
Subsection 2.1: Secure and Compliant
Security and compliance are paramount in today’s digital age. Azure AD B2B safeguards organizational data by enforcing conditional access policies and providing compliance data reporting, ensuring that collaborations do not compromise security.
Subsection 2.2: Simplified User Experience
Azure AD B2B curates a user-friendly environment for external partners, ensuring that collaborations are intuitive and productive, thereby reducing the learning curve and enhancing user engagement.
Subsection 2.3: Scalability
Whether it’s a small team collaboration or a large-scale B2B scenario, Azure AD B2B scales impeccably to meet diverse collaborative needs, ensuring that organizations can expand their collaborative horizons without technological constraints.
Section 3: Potential Downsides
Subsection 3.1: Complexity in Management
While Azure AD B2B offers a plethora of benefits, it brings along challenges such as managing external accounts, permissions, and ensuring regular audits to prevent unauthorized access.
Subsection 3.2: Cost Implications
Organizations need to meticulously plan and understand the cost implications, especially when dealing with extensive external users and resources, to ensure that the collaboration does not inadvertently strain financial resources.
Subsection 3.3: Dependency
Dependency on Azure implies that organizations might face limitations in terms of flexibility and control, which necessitates a thorough understanding and strategic planning before implementation.
Section 4: Getting Started with Azure AD B2B
Subsection 4.1: Ease of Setup
Azure AD B2B is renowned for its straightforward setup process, enabling organizations to implement it with minimal technical expertise.
Subsection 4.2: Step-by-Step Tutorial
- Sign in to the Microsoft Entra admin center as at least a External Identity Provider administrator.
- Browse to Identity > External Identities > External collaboration settings.
- Under Guest user access, choose the level of access you want guest users to have:
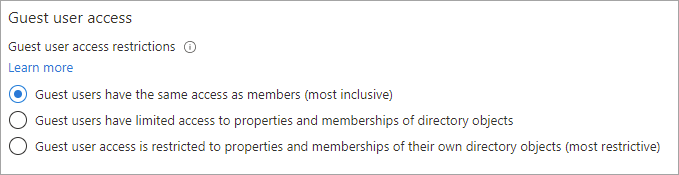
- Guest users have the same access as members (most inclusive): This option gives guests the same access to Microsoft Entra resources and directory data as member users.
- Guest users have limited access to properties and memberships of directory objects: (Default) This setting blocks guests from certain directory tasks, like enumerating users, groups, or other directory resources. Guests can see membership of all non-hidden groups. Learn more about default guest permissions.
- Guest user access is restricted to properties and memberships of their own directory objects (most restrictive): With this setting, guests can access only their own profiles. Guests aren’t allowed to see other users’ profiles, groups, or group memberships.
- Under Guest invite settings, choose the appropriate settings:
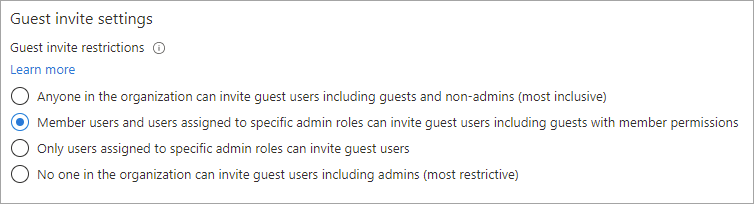
- Anyone in the organization can invite guest users including guests and non-admins (most inclusive): To allow guests in the organization to invite other guests including those who aren’t members of an organization, select this radio button.
- Member users and users assigned to specific admin roles can invite guest users including guests with member permissions: To allow member users and users who have specific administrator roles to invite guests, select this radio button.
- Only users assigned to specific admin roles can invite guest users: To allow only those users with administrator roles to invite guests, select this radio button. The administrator roles include Global Administrator, User Administrator, and Guest Inviter.
- No one in the organization can invite guest users including admins (most restrictive): To deny everyone in the organization from inviting guests, select this radio button.
- Under Enable guest self-service sign up via user flows, select Yes if you want to be able to create user flows that let users sign up for apps. For more information about this setting, see Add a self-service sign-up user flow to an app.

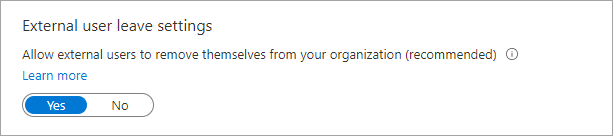
- Under External user leave settings, you can control whether external users can remove themselves from your organization. If you set this option to No, external users will need to contact your admin or privacy contact to be removed.
- Yes: Users can leave the organization themselves without approval from your admin or privacy contact.
- No: Users can’t leave your organization themselves. They’ll see a message guiding them to contact your admin or privacy contact to request removal from your organization.
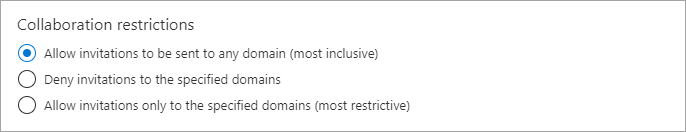
- Under Collaboration restrictions, you can choose whether to allow or deny invitations to the domains you specify and enter specific domain names in the text boxes. For multiple domains, enter each domain on a new line. For more information, see Allow or block invitations to B2B users from specific organizations.
Conclusion
Azure AD B2B emerges as a robust solution, bridging organizational boundaries and fostering secure, scalable, and seamless collaborations. As organizations navigate through the realms of digital collaborations, Azure AD B2B stands out as a beacon, guiding them towards enhanced productivity and secure inter-organizational connectivity.
